Cybersecurity & Data Privacy by Design (C|P) Principles
 |
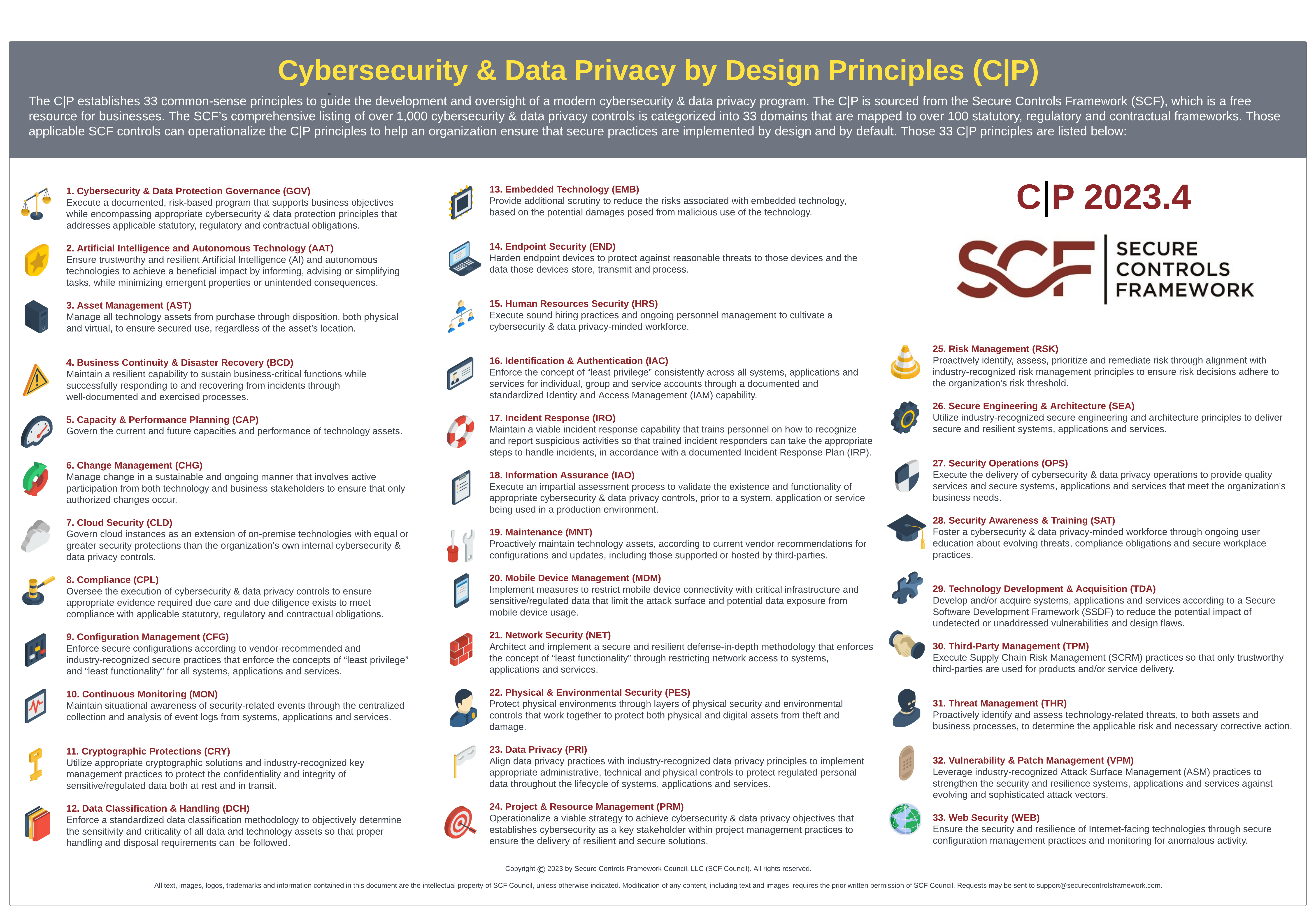
The concept of building security and privacy into technology solutions both by default and by design is a basic expectation for businesses, regardless of the industry. The adoption of cybersecurity and data privacy principles is a crucial step in building a secure, audit-ready program. The “C pipe P” logo is a nod to the computing definition of the | or “pipe” symbol (e.g., shift+backslash), which is a computer command line mechanism that allows the output of one process to be used as input to another process. In this way, a series of commands can be linked to more quickly and easily perform complex, multi-stage processing. Essentially, the concept is that cybersecurity principles are being “piped” with data privacy principles to create secure processes in an efficient manner. The C|P is a set of 33 security and privacy principles that leverage the SCF's extensive cybersecurity and data privacy control set. You can download the free poster by clicking the image to the right (updated for 2023). |
SCF Domains & Principles
| # | Icon | SCF Domain | SCF Identifier | Cybersecurity & Data Privacy by Design (C|P) Principles |
| 1 | Cybersecurity & Data Privacy Governance | GOV | Execute a documented, risk-based program that supports business objectives while encompassing appropriate cybersecurity and data privacy principles that addresses applicable statutory, regulatory and contractual obligations. | |
| 2 | |
Artificial and Autonomous Technology | AAT | Ensure trustworthy and resilient Artificial Intelligence (AI) and autonomous technologies to achieve a beneficial impact by informing, advising or simplifying tasks, while minimizing emergent properties or unintended consequences. |
| 3 | |
Asset Management | AST | Manage all technology assets from purchase through disposition, both physical and virtual, to ensure secured use, regardless of the asset’s location. |
| 4 | |
Business Continuity & Disaster Recovery | BCD | Maintain a resilient capability to sustain business-critical functions while successfully responding to and recovering from incidents through well-documented and exercised processes. |
| 5 | |
Capacity & Performance Planning | CAP | Govern the current and future capacities and performance of technology assets. |
| 6 | Change Management | CHG | Manage change in a sustainable and ongoing manner that involves active participation from both technology and business stakeholders to ensure that only authorized changes occur. | |
| 7 | Cloud Security | CLD | Govern cloud instances as an extension of on-premise technologies with equal or greater security protections than the organization’s own internal cybersecurity and privacy controls. | |
| 8 | |
Compliance | CPL | Oversee the execution of cybersecurity and data privacy controls to ensure appropriate evidence required due care and due diligence exists to meet compliance with applicable statutory, regulatory and contractual obligations. |
| 9 | |
Configuration Management | CFG | Enforce secure configurations for systems, applications and services according to vendor-recommended and industry-recognized secure practices. |
| 10 | |
Continuous Monitoring | MON | Maintain situational awareness of cybersecurity-related events through the centralized collection and analysis of event logs from systems, applications and services. |
| 11 | |
Cryptographic Protections | CRY | Utilize appropriate cryptographic solutions and industry-recognized key management practices to protect the confidentiality and integrity of sensitive/regulated data both at rest and in transit. |
| 12 | |
Data Classification & Handling | DCH | Enforce a standardized data classification methodology to objectively determine the sensitivity and criticality of all data and technology assets so that proper handling and disposal requirements can be followed. |
| 13 | |
Embedded Technology | EMB | Provide additional scrutiny to reduce the risks associated with embedded technology, based on the potential damages posed from malicious use of the technology. |
| 14 | |
Endpoint Security | END | Harden endpoint devices to protect against reasonable threats to those devices and the data those devices store, transmit and process. |
| 15 | |
Human Resources Security | HRS | Execute sound hiring practices and ongoing personnel management to cultivate a cybersecurity and privacy-minded workforce. |
| 16 | |
Identification & Authentication | IAC | Enforce the concept of “least privilege” consistently across all systems, applications and services for individual, group and service accounts through a documented and standardized Identity and Access Management (IAM) capability. |
| 17 | |
Incident Response | IRO | Maintain a viable incident response capability that trains personnel on how to recognize and report suspicious activities so that trained incident responders can take the appropriate steps to handle incidents, in accordance with a documented Incident Response Plan (IRP). |
| 18 | |
Information Assurance | IAO | Execute an impartial assessment process to validate the existence and functionality of appropriate cybersecurity and privacy controls, prior to a system, application or service being used in a production environment. |
| 19 | |
Maintenance | MNT | Proactively maintain technology assets, according to current vendor recommendations for configurations and updates, including those supported or hosted by third-parties. |
| 20 | |
Mobile Device Management | MDM | Implement measures to restrict mobile device connectivity with critical infrastructure and sensitive/regulated data that limit the attack surface and potential data exposure from mobile device usage. |
| 21 | |
Network Security | NET | Architect and implement a secure and resilient defense-in-depth methodology that enforces the concept of “least functionality” through restricting network access to systems, applications and services. |
| 22 | |
Physical & Environmental Security | PES | Protect physical environments through layers of physical security and environmental controls that work together to protect both physical and digital assets from theft and damage. |
| 23 | |
Data Privacy | PRI | Align data privacy practices with industry-recognized data privacy principles to implement appropriate administrative, technical and physical controls to protect regulated personal data throughout the lifecycle of systems, applications and services. |
| 24 | Project & Resource Management | PRM | Operationalize a viable strategy to achieve cybersecurity & privacy objectives that establishes cybersecurity as a key stakeholder within project management practices to ensure the delivery of resilient and secure solutions. | |
| 25 | |
Risk Management | RSK | Proactively identify, assess, prioritize and remediate risk through alignment with industry-recognized risk management principles to ensure risk decisions adhere to the organization's risk threshold. |
| 26 | |
Secure Engineering & Architecture | SEA | Utilize industry-recognized secure engineering and architecture principles to deliver secure and resilient systems, applications and services. |
| 27 | Security Operations | OPS | Execute the delivery of cybersecurity and privacy operations to provide quality services and secure systems, applications and services that meet the organization's business needs. | |
| 28 | |
Security Awareness & Training | SAT | Foster a cybersecurity and privacy-minded workforce through ongoing user education about evolving threats, compliance obligations and secure workplace practices. |
| 29 | |
Technology Development & Acquisition | TDA | Develop and test systems, applications or services according to a Secure Software Development Framework (SSDF) to reduce the potential impact of undetected or unaddressed vulnerabilities and design weaknesses. |
| 30 | |
Third-Party Management | TPM | Execute Supply Chain Risk Management (SCRM) practices so that only trustworthy third-parties are used for products and/or service delivery. |
| 31 | |
Threat Management | THR | Proactively identify and assess technology-related threats, to both assets and business processes, to determine the applicable risk and necessary corrective action. |
| 32 | Vulnerability & Patch Management | VPM | Leverage industry-recognized Attack Surface Management (ASM) practices to strengthen the security and resilience systems, applications and services against evolving and sophisticated attack vectors. | |
| 33 | |
Web Security | WEB | Ensure the security and resilience of Internet-facing technologies through secure configuration management practices and monitoring for anomalous activity. |