One Framework. Transparent Mapping. Defensible Security, Compliance & Resilience Controls.
The Secure Controls Framework (SCF) is a FREE, comprehensive cybersecurity and data privacy metaframework designed to help organizations build secure, compliant and resilient capabilities. Instead of managing multiple, overlapping laws, regulations and frameworks independently, the SCF normalizes requirements into a Common Controls Framework (CCF) that supports multiple statutory, regulatory and contractual compliance requirements.
The SCF utilizes Set Theory Relationship Mapping (STRM) from NIST IR 8477 to create defensible mappings, so there is transparency with the SCF that other frameworks lack. You can see for yourself why one or more SCF controls map to a requirement from a specific law, regulation or framework.
By normalizing controls across laws, regulations, and industry standards, the SCF enables organizations to reduce compliance complexity while improving security program effectiveness. The SCF helps organizations implement practical safeguards, generate defensible evidence of control effectiveness and demonstrate accountability to regulators, customers and other stakeholders.
With the SCF, cybersecurity becomes more than compliance, where it becomes a sustainable system for managing risk, protecting information and ensuring operational resilience in an increasingly complex threat and regulatory environment.
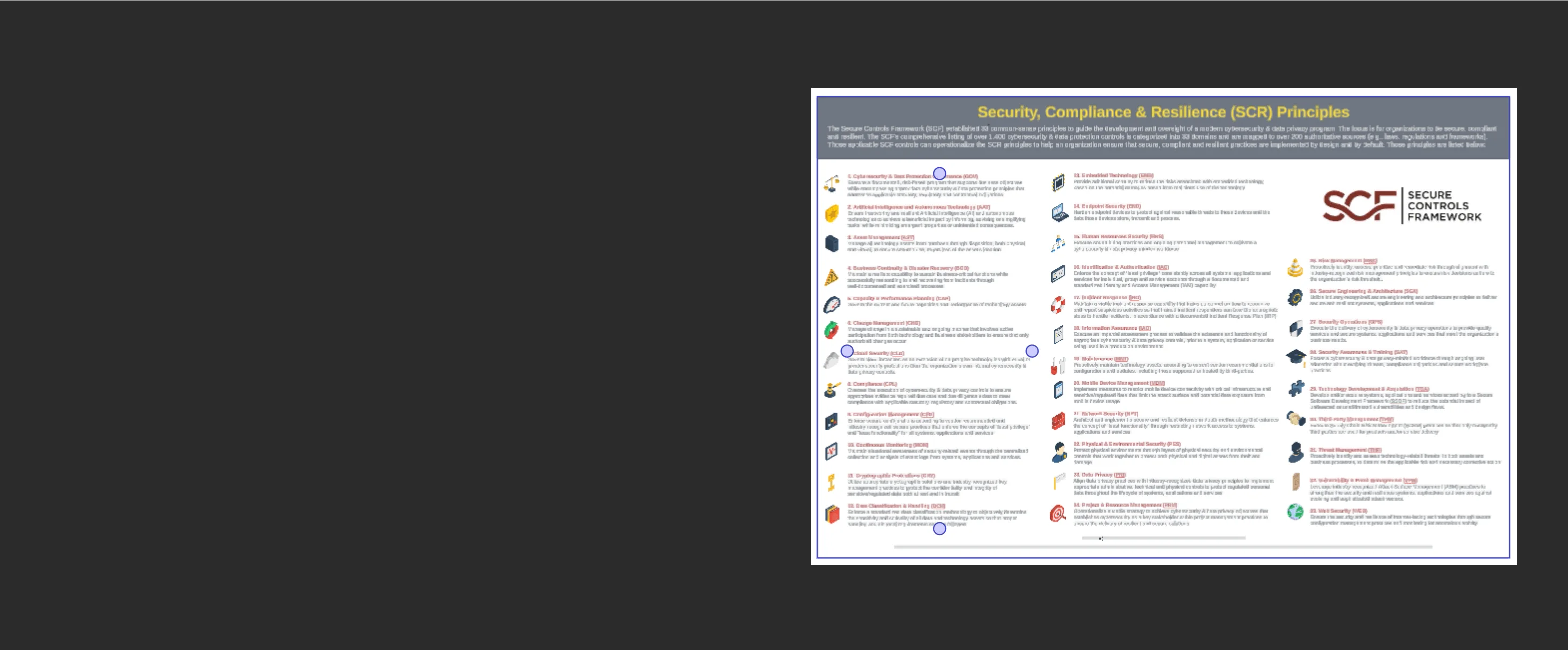
Cybersecurity, Compliance & Resilience Metaframework
The Common Controls Framework (CCF)
The Secure Controls Framework (SCF) Is A Free Resouce - Creative Commons Licensing Model
Simplify Cybersecurity. Strengthen Compliance. Build Resilience.
Regulators, auditors and customers increasingly require “Proof. Not promises” of security, compliance and resilience practices.
Cybersecurity is not just about preventing attacks, since it is about ensuring organizations can reasonably conduct business operations safely and securely, in addition to being able to recover from disruptions.
The SCF supports this effort by helping organizations implement controls in a way that generates defensible evidence that is objective proof that security, compliance and resilience capabilities are functioning as intended.
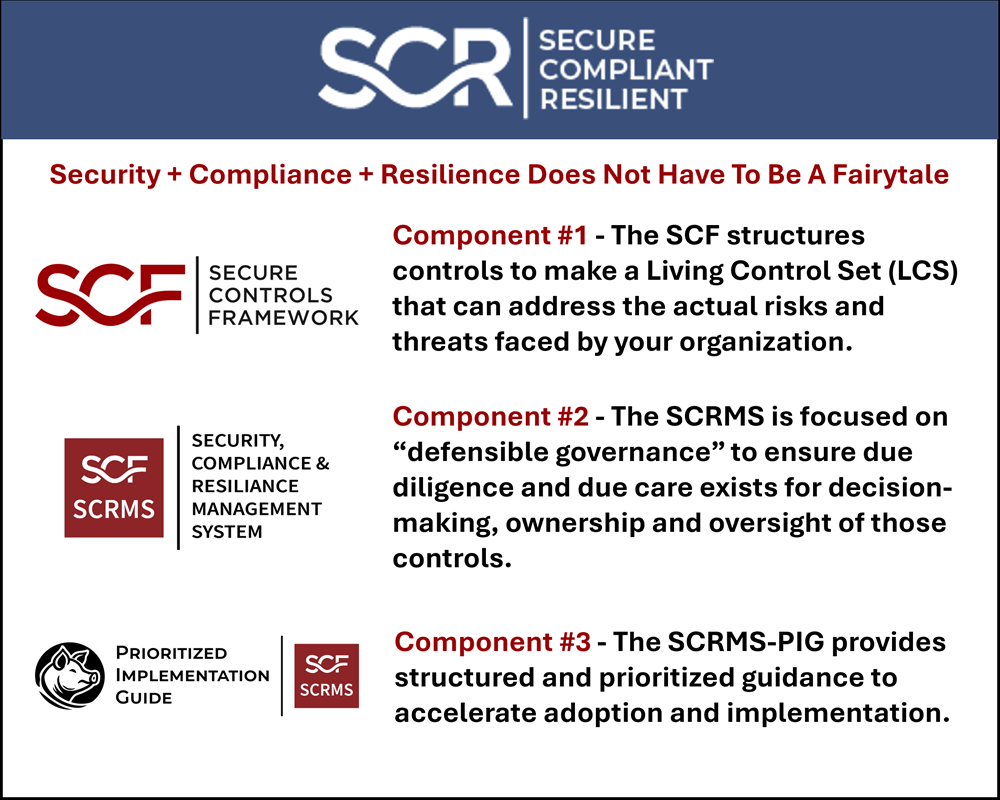
Security, Compliance & Resilience Management System (SCRMS)
The Security, Compliance & Resilience Management System (SCRMS) is a holistic, technology-agnostic approach to cybersecurity and data protection controls to identify, implement and manage Secure, Compliant and Resilient (SCR) capabilities, covering an entity’s People, Processes, Technologies, Data and Facilities (PPTDF), regardless of how or where data is stored, processed and/or transmitted.
The SCRMS enables an organization to align with one, or more, laws, regulations and/or frameworks. For example, an organization that aligns with NIST CSF 2.0, but also has obligations for PCI DSS, ISO 27001, ISO 42001, HIPAA Security Rule and SOC 2 can leverage a “living control set” that is capable of adjusting to the specific security, compliance and resilience requirements it must address.
The SCRMS is not a “one-size-fits-all” playbook, since the information in this document is meant to be adopted and tailored to the organization's unique size, resources and risk circumstances. Additionally, the SCRMS comes with a companion document, the SCRMS Prioritized Implementation Guide (SCRMS-PIG) that is a "paint by numbers" approach to implementing the SCF.
Our Story
A little bit about the Secure Controls Framework (SCF)