SCF Certification - Conformity Assessment Program (CAP)
We are pleased to announce that an organization-level certification program is coming for the SCF and we expect this to launch in Q1 2023.
The Secure Controls Framework Conformity Assessment Program (SCF CAP) is an organization-level conformity assessment. The SCF CAP is designed to utilize tailored cybersecurity and privacy controls that specifically address the applicable statutory, regulatory and contractual obligations an Organization Seeking Certification (OSC) is required to comply with. By using the metaframework nature of the SCF, an OSC is able to perform conformity assessment that spans multiple cybersecurity and privacy-specific laws, regulations and frameworks.
By Cybersecurity Professionals. For Cybersecurity Professionals.
The SCF CAP is an organization-level conformity assessment. The SCF CAP is designed to utilize tailored cybersecurity and privacy controls that specifically address the applicable statutory, regulatory and contractual obligations an Organization Seeking Certification (OSC) is required to comply with. By using the metaframework nature of the SCF, an OSC is able to perform conformity assessment that spans multiple cybersecurity and privacy-specific laws, regulations and frameworks.
Earning a SCF Certified™ designation is meant to signify an accomplishment, rather than be viewed as a “participation ribbon” that has little practical value for the OSC or stakeholders in the OSC’s supply chain to understand the OSC’s security posture.
The SCF CAP is focused on using the SCF as the control set to provide a company-level certification. While the SCF-CAP shares some similarities with other existing, single-focused certifications (e.g., ISO 27001, CMMC, FedRAMP, etc.), the SCF CAP is unique in its metaframework approach to covering cybersecurity and data protection requirements that span multiple laws, regulations and frameworks
SCF Certified - Third-Party Validation of SCF Control Conformity
Regardless of the industry, there is a definitive need for a third-party verified certification that assesses tailored cybersecurity and privacy controls that could impact the OSC and its supply chain stakeholders. The SCF CAP was designed to deliver an organization-level certification that is industry-recognized, earned through a qualified third-party assessor’s review of supporting evidence of a control’s effectiveness.
As cybersecurity and data protection operations are multi-faceted, the SCF CAP is designed to ensure that assessed controls reflect the real-world requirements faced by the OSC from a statutory, regulatory and contractual perspective. An assessment that only covers a part of an OSC’s cybersecurity and privacy program results in an inaccurate and incomplete report on the OSC’s overall security posture, providing a false sense of security to the OSC.
The SCF CAP is designed for cybersecurity & privacy practitioners by cybersecurity & privacy practitioners. This concept is based on the need within the industry for a tailored conformity assessment solution that is capable of addressing several key considerations:
- View compliance as a natural by-product of secure practices;
- Scale to address multifaceted operational requirements (e.g., laws, regulations and frameworks);
- Acknowledge the stated risk tolerance of the OSC since not all organizations have the same risk tolerance;
- Minimize the risk of “gaming” the certification process that provides no useful insights into the security posture of the OSC;
- Utilize technology to make the assessment process more efficient to drive down labor-related assessment costs; and
- Leverage existing industry recognized practices, where possible.
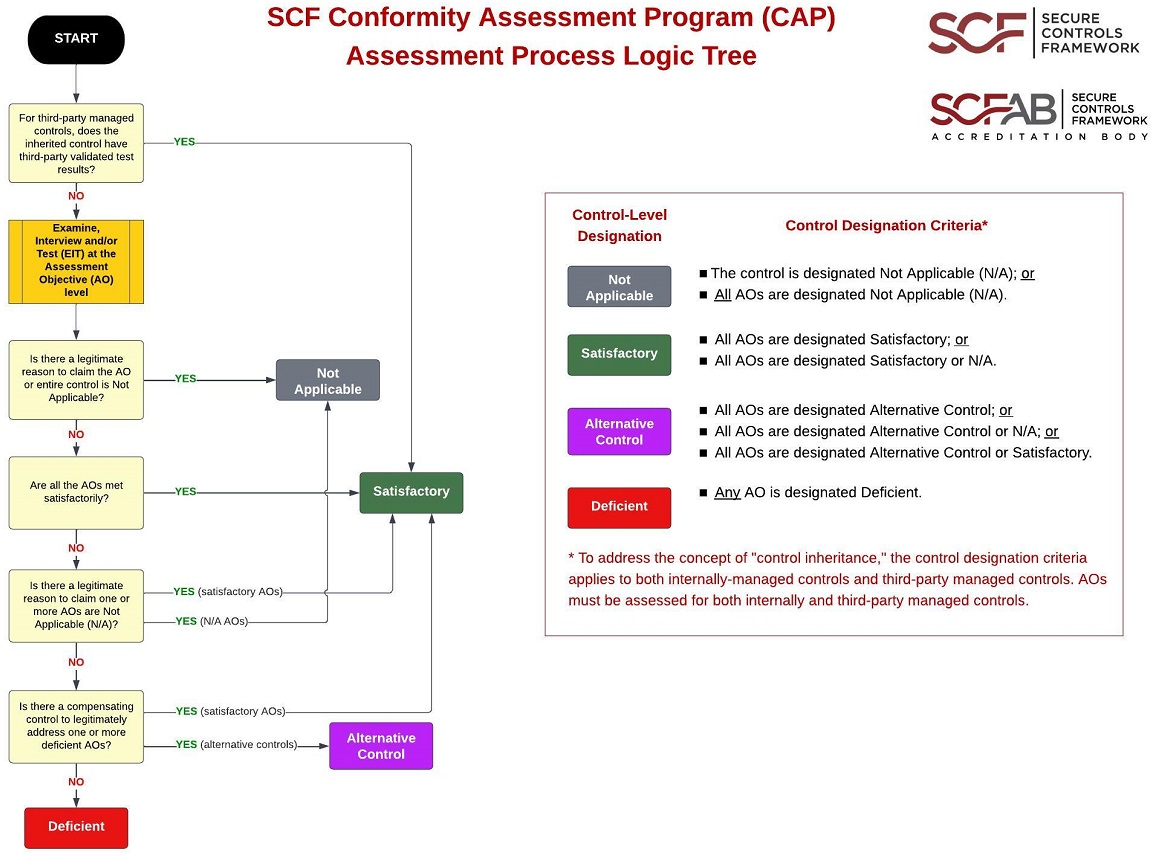
SCF Conformity Assessment Process Logic Tree
The following diagram can help visual the concept of determining the "pass / fail" status of a control (you can click on the image for a PDF version):
SCF Certification
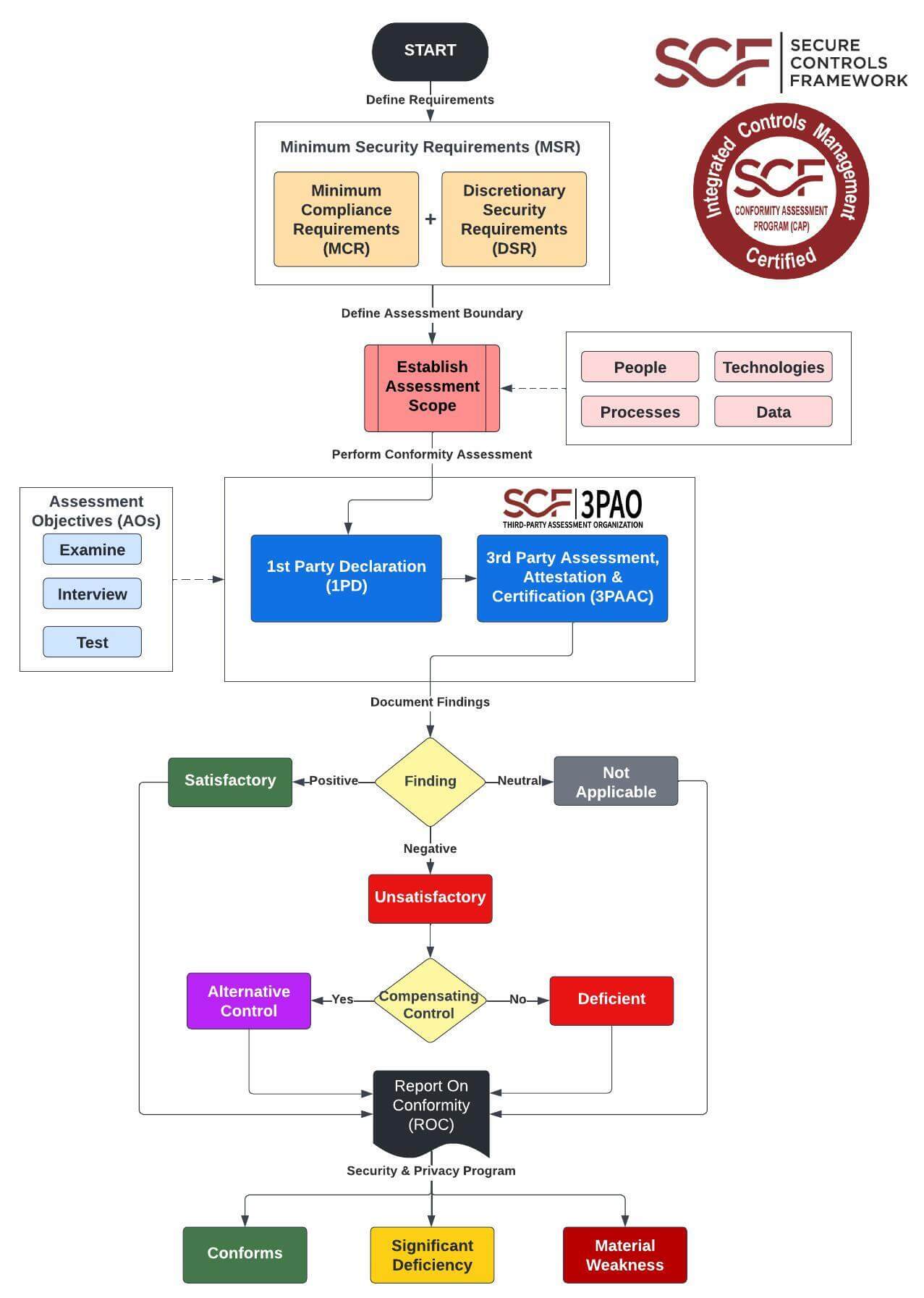
SCF Certification is valid for two (2) years from the date the OSC earns the SCF Certified™ designation, with the requirement for annual passing self-attestation through a First Party Declaration (1PD) to maintain the SCF Certified™ designation. The CAP is designed to produce an deliverable Report on Conformity (ROC) that indicate one of three outcomes that describes the overall organization's cybersecurity and privacy program:
1. Conforms.
- This is a positive outcome.
- This indicates that at a high-level, the organization’s cybersecurity and privacy practices conform to its selected cybersecurity and privacy practices. At the control level, there may be one or more deficient controls, but as a whole, the cybersecurity and privacy practices support the organization’s stated risk tolerance
- It is a statement that the assessed controls conform indicates to the organization’s management that sufficient evidence of due care and due diligence exists to assure that the organization’s stated risk tolerance can be achieved.
2. Significant Deficiency.
- This is a negative outcome and indicates the organization was unable to demonstrate conformity with its selected cybersecurity and privacy practices, due to systematic problems. Further, this indicates cybersecurity and privacy practices fail to support the organization’s stated risk tolerance. This is less severe than a material weakness, but merits executive leadership attention.
- It is a statement that the assessed controls have a significant deficiency indicates to the organization’s management that insufficient evidence of due care and due diligence exists to assure that the organization’s stated risk tolerance is achieved, due to a systemic problem in the cybersecurity and/or privacy program.
- In the context of a significant deficiency, a systemic problem is a consequence of issues inherent in the overall function (e.g., team, department, project, application, service, vendor, etc.), rather than a specific, isolated factor. Systemic errors may require changing the structure, personnel, technology and/or practices to remediate the significant deficiency.
3. Material Weakness.
- This is a negative outcome and indicates the organization is unable to demonstrate conformity with its selected cybersecurity and privacy practices, due to deficiencies that make it probable that reasonable-expected threats will not be prevented or detected in a timely manner that directly, or indirectly, affects assurance that the organization can adhere to its stated risk tolerance.
- A material weakness indicates cybersecurity and privacy practices fail to support the organization’s stated risk tolerance.
- It is a statement that the assessed controls have a material weakness indicates to the organization’s management that deficiencies are grave enough that it improbable that reasonable threats will be prevented or detected in a timely manner that directly, or indirectly, affects assurance that the organization can adhere to its own stated risk tolerance. Essentially, the security and privacy program is incapable of performing its stated mission and drastic changes to people, processes and/or technology are necessary to remediate the findings.
A Focus on Being Able To Demonstrate Security & Privacy by Design (SPbD)
The concept of being able to demonstrate evidence of both security and privacy by design (SPbD) is growing in importance with regulations such as the European Union General Data Protection Regulation (EU GDPR).
- The SCF’s Security & Privacy by Design Principles (S|P) provides thirty-two (32) principles that are able to be reported on, based on the controls associated with each of those principles.
- The applicable controls form the MSR, as defined by the applicable statutory, regulatory and contractual obligations the client wants to be assessed against. The result of these controls should provide evidence of SPbD.
In an effort to avoid re-inventing the wheel, the CAP will leverage NIST’s Risk Management Framework (RMF) as a way to scope the lifecycle of security and privacy controls. The RMF consists of six (6) unique phases and the CAP will cover the lifecycle of controls management:
- Categorize systems
- Select security & privacy controls
- Implement security & privacy controls
- Assess security & privacy controls
- Authorize systems, applications & services
- Monitor security & privacy controls.
During the SCF Certification process, SCF Assessors will primarily evaluate:
- How systems/processes/services are categorized;
- The security and privacy controls that were selected;
- The efficacy of how the security and privacy controls were implemented;
- The method that security and privacy by design principles were assessed, prior to systems/services/applications going into production; and
- The ongoing monitoring of security and privacy controls.
SCF Assessors will also evaluate controls deemed by a client to be not applicable or identify compensating controls for where the organization has accepted the risk not to implement a SCF control.
SCF CAP Ecosystem
The SCF CAP Ecosystem is made up of several parties:
- SCF Third Party Assessment Organization (SCF 3PAO). These are the organizations that conduct SCF Certification services.
- SCF Assessor (SCF Assessor). These are individuals who work for SCF 3PAOs to perform SCF Certification services.
- SCF Practitioner (SCF Practitioner). These are individuals who are experienced with the SCF and can help organizations tailor, implement and maintain SCF controls.
- Organizations Seeking Certification (OSC). The OSC are the organizations that hire the SCF 3PAO to perform an SCF Certification for their specific business.